
Security Risk Assessment - An Unavoidable Check for Businesses
When encountering a natural or man-made disaster, organizations' existing IT security controls play the most crucial part. Businesses focusing less...
Learn More
The digital age has significantly increased the challenge of managing sensitive data for businesses. The fast-paced digitization, adoption of Artificial Intelligence (AI), and automation are becoming the catalysts for unprecedented increases in data manipulation. Without robust security measures, businesses face a multitude of threats, including data breaches, identity theft, and ransomware attacks, potentially jeopardizing their entire operation.
The importance of robust information security program development and management cannot be overstated. A well-planned and executed strategy enables your organization to leverage an all-inclusive protection approach for Personally Identifiable Information (PII), Protected Health Information (PHI), sensitive company credentials/documents, and more.
This article covers the life cycle, steps to build and implement, and benefits of information security program development.


An information security program is a comprehensive framework encompassing your organization's IT infrastructure, policies, projects, goals, and strategies to protect its data and assets. It protects your key enterprise operations, networks, in-house data handling systems, assets, and employees from prying eyes. Information security programs also aid in swiftly identifying individuals and loopholes within IT infrastructures that compromise security.
The information security program lifecycle consists of six comprehensive phases to effectively manage and protect digital assets, uphold confidentiality, and bolster trust. These include:
The initial phase of the Information Security Lifecycle is planning, where you formulate your information security policies and procedures. This involves conducting thorough risk assessments to pinpoint potential threats and vulnerabilities. By laying down a solid foundation for information security program development and management, you can establish the framework upon which security strategies will be built.
Following the planning phase comes implementation. This stage involves your organization translating its security policies and procedures into action. Key activities include employee training on security protocols and deploying the requisite software and hardware infrastructure. Through effective implementation, you can strengthen your defenses against potential security breaches.
The operational phase is where your organization executes its day-to-day activities in alignment with established protocols in information security programs. It involves the continual adherence to security policies while conducting routine operations. Additionally, this phase encompasses the vigilant monitoring of network activities to detect any anomalies or security breaches promptly.
In the monitoring phase, you conduct regular assessments of security procedures and actively monitor network activities for any deviations from the set standards. This ongoing surveillance aids in the early detection of potential security threats, enabling you to take proactive measures to mitigate risks. Moreover, the insights gained from monitoring inform refinements to the security system, enhancing its effectiveness over time.
Maintenance constitutes the fifth phase of the Information Security Programs Lifecycle. Here, you focus on updating and fine-tuning your security policies and procedures in response to evolving threats, changing organizational requirements, and stringent regulatory obligations. Regular testing of the security infrastructure ensures its continued efficacy and resilience against emerging vulnerabilities.
The final phase, disposal, involves securely disposing of all data and information associated with your security system. Proper disposal measures are crucial to prevent sensitive data from falling into the wrong hands once it is no longer needed. By systematically decommissioning outdated systems and securely erasing sensitive information, you can mitigate the risk of data breaches and maintain compliance with regulatory standards.
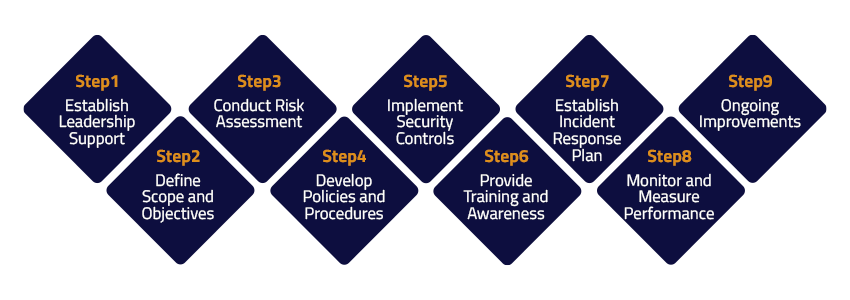
Building a robust information security program requires careful planning and execution. Here are nine essential steps to guide your organization through the process:
Convey and ask for commitment from senior management to prioritize information security and allocate necessary resources.
Clearly outline the scope of the information security program development and management with measurable objectives aligned with your organization’s goals.
Identify and assess potential known and emerging risks and vulnerabilities to determine your organization's security posture precisely and comprehensively.
Create comprehensive policies and procedures that address information security requirements, compliance standards, and industry best practices.
Deploy appropriate technical and administrative controls to mitigate identified risks and enforce compliance with regulatory policies such as HIPAA, GDPR, FISMA, ISO 270001, PCI DSS, etc.
Educate employees with certifications and training about security protocols, industry best practices, emerging cyber threats, and their role in maintaining information security.
Develop a robust incident response plan to address and mitigate security incidents effectively, such as Zero Day, Ransomware, Phishing, and Data Breach attacks, in case these occur.
Implement mechanisms for ongoing monitoring, evaluation, and reporting of the information security program's effectiveness.
Regularly review and update the information security program and data protection strategies to adapt to evolving threats, technologies, and regulatory requirements.
Effective information security program development and management offers visible and long-term benefits, including risk mitigation, compliance adherence, reputation protection, cost savings, and competitive advantage. It ensures resilience against cyber threats, preserves organizational integrity, and fosters trust in today's digital landscape.
By identifying and mitigating security risks, effective information security program management minimizes the likelihood and impact of data breaches, cyberattacks, and operational disruptions. This proactive approach enables you to guard sensitive data and preserve business continuity while cutting down on financial losses associated with security incidents.
An effective information security program ensures compliance with strengthening regulatory obligations and industry standards, both regional and international, such as GDPR, HIPAA, FISMA, and PCI DSS. By adhering to these regulations, organizations avoid costly penalties, scrutiny, legal consequences, and black or gray listing while also demonstrating a commitment to protecting customer data and privacy.
Strong security measures inspire trust and confidence among customers, partners, and stakeholders. By safeguarding sensitive information and preventing data breaches, you can uphold your organization’s reputation and brand integrity, fostering long-term relationships and loyalty.
Preventing data breaches and security incidents can result in significant cost and resource savings for your organization. By avoiding financial losses, litigation expenses, regulatory fines, and reputational damage associated with security breaches, effective information security program development and management contributes to the overall financial health and stability of your enterprise.
Organizations with robust information security programs gain a competitive edge in the marketplace. By ensuring security excellence, they attract customers who prioritize data protection and privacy. This competitive advantage helps differentiate your organization from competitors and positions it as a trusted partner in the digital landscape.
In conclusion, effective information security program development and management is essential for safeguarding your organization against the evolving threat landscape. By prioritizing risk assessment, establishing clear policies and procedures, investing in employee training, implementing robust access controls, preparing for incident response, and continuously monitoring and improving security measures, you can maximize your enterprise’s resilience to cyber threats.
Curate and strengthen your organization's security posture with Ferro Technics, a leading cybersecurity consulting services provider in the USA and Canada. Benefit from expert guidance in developing an information security program tailored to your needs. Our proven track record of almost a decade ensures unwavering assistance in building robust defenses, achieving regulatory compliance, and safeguarding your digital assets effectively.

When encountering a natural or man-made disaster, organizations' existing IT security controls play the most crucial part. Businesses focusing less...
Learn More
On average, around 2,200 cyberattacks are launched every day. The increased usage of cloud solutions, third-party transactions, and overall digitiz...
Learn More
In an era of interconnected technologies, the digital landscape presents both unprecedented opportunities and formidable challenges. As organizatio...
Learn More
In the current era of advanced technology, where cyber-criminals and hackers are finding new ways to infiltrate systems and steal sensitive data, e...
Learn More
In the rapidly evolving digital landscape where advanced technologies such as Artificial Intelligence (AI), Deep Learning, Machine Learning (ML), B...
Learn More
The results of a joint study by Jeff Hancock (Professor at Stanford University) and Tessian, a security company, show that human error or employee ...
Learn More
The cybersecurity industry has recently undergone rapid growth and global-level expansion like no other sector, estimated to grow from $190.5 billi...
Learn More
Our digital world is a double-edged sword. While it offers incredible opportunities, it also exposes us to unseen dangers. Cybersecurity fundamenta...
Learn More
Vulnerability assessment is the systematic review of network ...
Learn More
In the dynamic and constantly evolving field of cybersecurity, maintaining a proactive stance against emerging threats necessitates a comprehensive...
Learn More
Obtaining industry-recognized certifications is a powerful way to showcase your expertise, enhance your credibility, and unlock new caree...
Learn More
In today’s digitally-driven world, cybersecurity has become a critical component for organizations across all sectors. The growing ...
Learn More
Have you ever wondered how you can become a cybersecurity expert and significantly advance your career? If yes, ...
Learn More