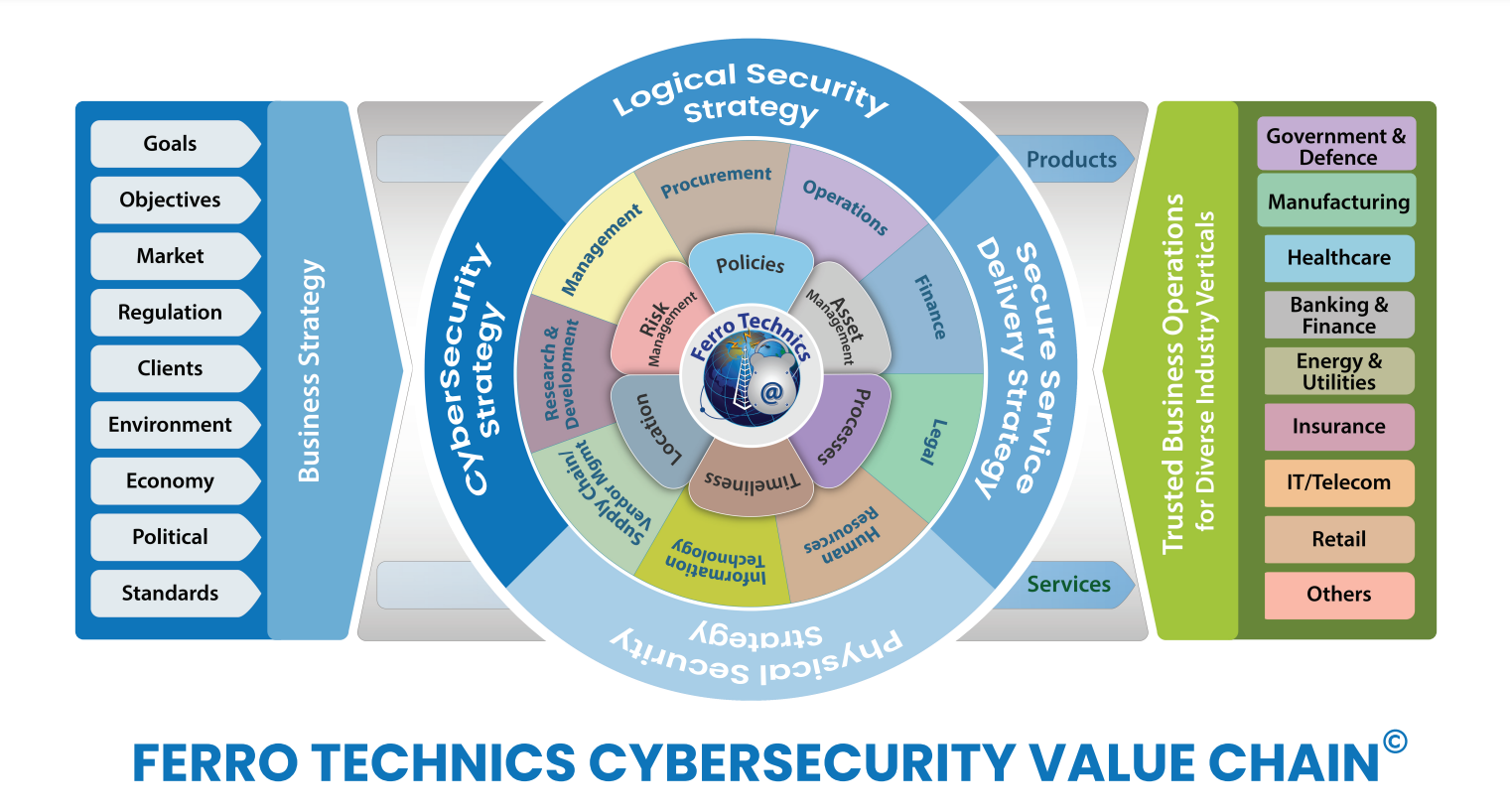
Ferro Technics is Your Trusted Partner in Compliance Management
With experience of over seven years in providing IT auditing and
consulting services to businesses and conducting security awareness
training, Ferro Technics has become a highly reputed name in the IT
industry. We are a leading cybersecurity services and training
provider to organizations.
We aim to empower the financial, education, and health sectors in
building robust data security systems capable of detecting,
deterring and managing potential risks to mitigate their impact on
organization’s assets including goodwill, and reputation.
Cybersecurity threats and compliance management continue to evolve
in intricacy, with more and more stringent measures being
supplemented to the legal framework. At Ferro Technics, we
understand multifaceted challenges businesses face in aligning
information security infrastructures with compliance requirements.
We extend our auditing and consulting services for cybersecurity,
risk management and cloud security, comprehending the clients’
real-time experiences in developing a cyber-aware infrastructure.
Learn More

 EC-COUNCIL
EC-COUNCIL
 PECB
PECB



.png)

.png)